作者论坛账号:wykdz
题目打包下载地址:
https://down.52pojie.cn/Challenge/Happy_New_Year_2019_Challenge.rar
第三题 逆向题(od方式)
1.od打开程序,运行,查找字符串,到最后会发现一行有用的。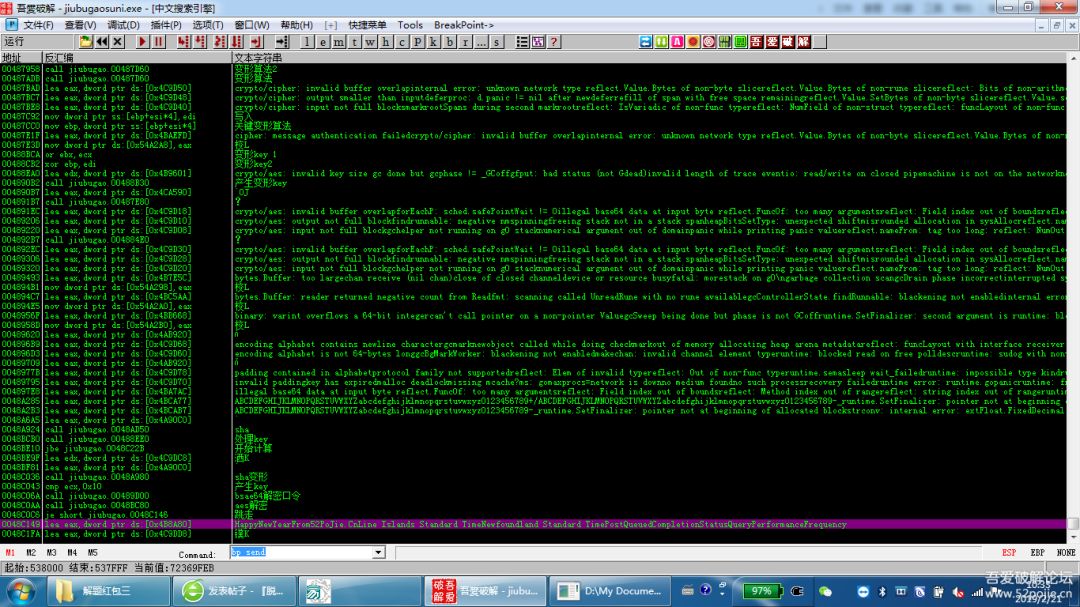
点到代码出,向上观察,找到跳转,发现
0048C0C3 . 83F9 1A cmp ecx,0x1A
0048C0C6 . 74 7E je short jiubugao.0048C146 ; 跳走
两行代码,猜测最终文本应该是26个(0x1A),也就是HappyNewYearFrom52PoJie.Cn
2.判断加密算法,首先粗略判断,打开PEID和插件查看加密算法,有sha,aes,base64这么三种。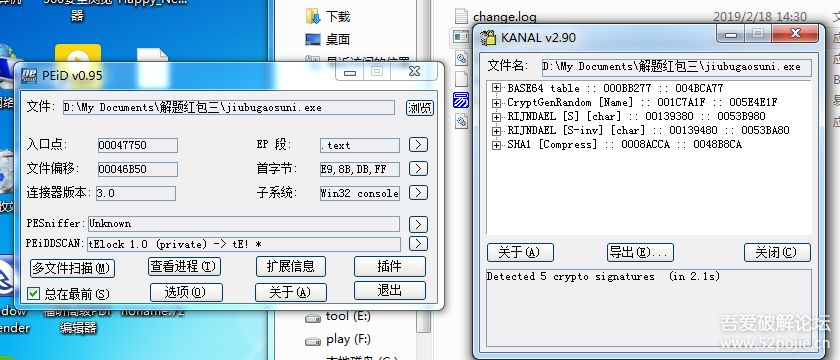
3.在关键字符串出现的程序段,开头下断点,运行程序,一直f8,直到程序跑起来,输入uid,再f8到程序跑起来,输入假口令【SGFwcHlOZXdZZWFyRnJvbTUyUG9KaWUuQ24=】,看下每个call的返回,会发现该段程序就是口令判断的主要过程。逐条分析,主要注释如下:
0048BE00 > /64:8B0D 14000>mov ecx,dword ptr fs:[0x14] ; jiubugao.0054A970
0048BE07 . |8B89 00000000 mov ecx,dword ptr ds:[ecx]
0048BE0D . |3B61 08 cmp esp,dword ptr ds:[ecx+0x8]
0048BE10 . |0F86 15040000 jbe jiubugao.0048C22B ; 开始计算
0048BE16 . |83EC 7C sub esp,0x7C
0048BE19 . |C74424 74 000>mov dword ptr ss:[esp+0x74],0x0
0048BE21 . |C74424 78 000>mov dword ptr ss:[esp+0x78],0x0
0048BE29 . |8D05 E0044A00 lea eax,dword ptr ds:[0x4A04E0]
0048BE2F . |894424 74 mov dword ptr ss:[esp+0x74],eax
0048BE33 . |8D0D C09D4C00 lea ecx,dword ptr ds:[0x4C9DC0]
0048BE39 . |894C24 78 mov dword ptr ss:[esp+0x78],ecx
0048BE3D . |8D4C24 74 lea ecx,dword ptr ss:[esp+0x74]
0048BE41 . |890C24 mov dword ptr ss:[esp],ecx
0048BE44 . |C74424 04 010>mov dword ptr ss:[esp+0x4],0x1
0048BE4C . |C74424 08 010>mov dword ptr ss:[esp+0x8],0x1
0048BE54 . |E8 57FCFEFF call jiubugao.0047BAB0
0048BE59 . |8D05 E0044A00 lea eax,dword ptr ds:[0x4A04E0]
0048BE5F . |890424 mov dword ptr ss:[esp],eax
0048BE62 . |E8 29D5F7FF call jiubugao.00409390
0048BE67 . |8B4424 04 mov eax,dword ptr ss:[esp+0x4] ; KernelBa.76B9F0CC
0048BE6B . |894424 34 mov dword ptr ss:[esp+0x34],eax
0048BE6F . |8D0D E0044A00 lea ecx,dword ptr ds:[0x4A04E0]
0048BE75 . |890C24 mov dword ptr ss:[esp],ecx
0048BE78 . |E8 13D5F7FF call jiubugao.00409390
0048BE7D . |8B4424 04 mov eax,dword ptr ss:[esp+0x4] ; KernelBa.76B9F0CC
0048BE81 . |894424 38 mov dword ptr ss:[esp+0x38],eax
0048BE85 . |C74424 6C 000>mov dword ptr ss:[esp+0x6C],0x0
0048BE8D . |C74424 70 000>mov dword ptr ss:[esp+0x70],0x0
0048BE95 . |8D0D E0044A00 lea ecx,dword ptr ds:[0x4A04E0]
0048BE9B . |894C24 6C mov dword ptr ss:[esp+0x6C],ecx
0048BE9F . |8D15 C89D4C00 lea edx,dword ptr ds:[0x4C9DC8] ; 洒K
0048BEA5 . |895424 70 mov dword ptr ss:[esp+0x70],edx
0048BEA9 . |8D5424 6C lea edx,dword ptr ss:[esp+0x6C]
0048BEAD . |891424 mov dword ptr ss:[esp],edx
0048BEB0 . |C74424 04 010>mov dword ptr ss:[esp+0x4],0x1
0048BEB8 . |C74424 08 010>mov dword ptr ss:[esp+0x8],0x1
0048BEC0 . |E8 BBFAFEFF call jiubugao.0047B980
0048BEC5 . |C74424 64 000>mov dword ptr ss:[esp+0x64],0x0
0048BECD . |C74424 68 000>mov dword ptr ss:[esp+0x68],0x0
0048BED5 . |8D05 E08E4900 lea eax,dword ptr ds:[0x498EE0]
0048BEDB . |894424 64 mov dword ptr ss:[esp+0x64],eax
0048BEDF . |8B4C24 34 mov ecx,dword ptr ss:[esp+0x34]
0048BEE3 . |894C24 68 mov dword ptr ss:[esp+0x68],ecx
0048BEE7 . |8D5424 64 lea edx,dword ptr ss:[esp+0x64]
0048BEEB . |891424 mov dword ptr ss:[esp],edx
0048BEEE . |C74424 04 010>mov dword ptr ss:[esp+0x4],0x1
0048BEF6 . |C74424 08 010>mov dword ptr ss:[esp+0x8],0x1
0048BEFE . |E8 6D68FFFF call jiubugao.00482770
0048BF03 . |C74424 5C 000>mov dword ptr ss:[esp+0x5C],0x0
0048BF0B . |C74424 60 000>mov dword ptr ss:[esp+0x60],0x0
0048BF13 . |8D05 E0044A00 lea eax,dword ptr ds:[0x4A04E0]
0048BF19 . |894424 5C mov dword ptr ss:[esp+0x5C],eax
0048BF1D . |8D0D D09D4C00 lea ecx,dword ptr ds:[0x4C9DD0]
0048BF23 . |894C24 60 mov dword ptr ss:[esp+0x60],ecx
0048BF27 . |8D4C24 5C lea ecx,dword ptr ss:[esp+0x5C]
0048BF2B . |890C24 mov dword ptr ss:[esp],ecx
0048BF2E . |C74424 04 010>mov dword ptr ss:[esp+0x4],0x1
0048BF36 . |C74424 08 010>mov dword ptr ss:[esp+0x8],0x1
0048BF3E . |E8 3DFAFEFF call jiubugao.0047B980
0048BF43 . |C74424 54 000>mov dword ptr ss:[esp+0x54],0x0
0048BF4B . |C74424 58 000>mov dword ptr ss:[esp+0x58],0x0
0048BF53 . |8D05 E08E4900 lea eax,dword ptr ds:[0x498EE0]
0048BF59 . |894424 54 mov dword ptr ss:[esp+0x54],eax
0048BF5D . |8B4C24 38 mov ecx,dword ptr ss:[esp+0x38]
0048BF61 . |894C24 58 mov dword ptr ss:[esp+0x58],ecx
0048BF65 . |8D5424 54 lea edx,dword ptr ss:[esp+0x54]
0048BF69 . |891424 mov dword ptr ss:[esp],edx
0048BF6C . |C74424 04 010>mov dword ptr ss:[esp+0x4],0x1
0048BF74 . |C74424 08 010>mov dword ptr ss:[esp+0x8],0x1
0048BF7C . |E8 EF67FFFF call jiubugao.00482770
0048BF81 . |8D05 C0904A00 lea eax,dword ptr ds:[0x4A90C0] ; `
0048BF87 . |890424 mov dword ptr ss:[esp],eax
0048BF8A . |E8 01D4F7FF call jiubugao.00409390
0048BF8F . |8B4424 04 mov eax,dword ptr ss:[esp+0x4] ; KernelBa.76B9F0CC
0048BF93 . |894424 30 mov dword ptr ss:[esp+0x30],eax
0048BF97 . |C700 01234567 mov dword ptr ds:[eax],0x67452301
0048BF9D . |C740 04 89ABC>mov dword ptr ds:[eax+0x4],0xEFCDAB89
0048BFA4 . |C740 08 FEDCB>mov dword ptr ds:[eax+0x8],0x98BADCFE
0048BFAB . |C740 0C 76543>mov dword ptr ds:[eax+0xC],0x10325476
0048BFB2 . |C740 10 F0E1D>mov dword ptr ds:[eax+0x10],0xC3D2E1F0
0048BFB9 . |C740 54 00000>mov dword ptr ds:[eax+0x54],0x0
0048BFC0 . |C740 58 00000>mov dword ptr ds:[eax+0x58],0x0
0048BFC7 . |C740 5C 00000>mov dword ptr ds:[eax+0x5C],0x0
0048BFCE . |8B4C24 34 mov ecx,dword ptr ss:[esp+0x34]
0048BFD2 . |8B51 04 mov edx,dword ptr ds:[ecx+0x4]
0048BFD5 . |8B09 mov ecx,dword ptr ds:[ecx]
0048BFD7 . |894C24 04 mov dword ptr ss:[esp+0x4],ecx
0048BFDB . |895424 08 mov dword ptr ss:[esp+0x8],edx
0048BFDF . |C70424 000000>mov dword ptr ss:[esp],0x0
0048BFE6 . |E8 C5B2FAFF call jiubugao.004372B0
0048BFEB . |8D05 A0A64C00 lea eax,dword ptr ds:[0x4CA6A0]
0048BFF1 . |8400 test byte ptr ds:[eax],al
0048BFF3 . |8B4424 0C mov eax,dword ptr ss:[esp+0xC] ; ntdll_12.77C458C5
0048BFF7 . |8B4C24 10 mov ecx,dword ptr ss:[esp+0x10]
0048BFFB . |8B5424 14 mov edx,dword ptr ss:[esp+0x14]
0048BFFF . |894424 04 mov dword ptr ss:[esp+0x4],eax
0048C003 . |894C24 08 mov dword ptr ss:[esp+0x8],ecx
0048C007 . |895424 0C mov dword ptr ss:[esp+0xC],edx
0048C00B . |8B4424 30 mov eax,dword ptr ss:[esp+0x30]
0048C00F . |890424 mov dword ptr ss:[esp],eax
0048C012 . |E8 59E7FFFF call jiubugao.0048A770
0048C017 . |C74424 04 000>mov dword ptr ss:[esp+0x4],0x0
0048C01F . |C74424 08 000>mov dword ptr ss:[esp+0x8],0x0
0048C027 . |C74424 0C 000>mov dword ptr ss:[esp+0xC],0x0
0048C02F . |8B4424 30 mov eax,dword ptr ss:[esp+0x30]
0048C033 . |890424 mov dword ptr ss:[esp],eax
0048C036 . |E8 45E9FFFF call jiubugao.0048A980 ; sha变形
0048C03B . |8B4424 10 mov eax,dword ptr ss:[esp+0x10]
0048C03F . |8B4C24 18 mov ecx,dword ptr ss:[esp+0x18]
0048C043 . |83F9 10 cmp ecx,0x10 ; 看eax的地址
0048C046 . |0F82 D8010000 jb jiubugao.0048C224
0048C04C . |894424 2C mov dword ptr ss:[esp+0x2C],eax
0048C050 . |8B4424 38 mov eax,dword ptr ss:[esp+0x38]
0048C054 . |8B48 04 mov ecx,dword ptr ds:[eax+0x4]
0048C057 . |8B00 mov eax,dword ptr ds:[eax]
0048C059 . |894424 04 mov dword ptr ss:[esp+0x4],eax
0048C05D . |894C24 08 mov dword ptr ss:[esp+0x8],ecx
0048C061 . |8B05 D89E5400 mov eax,dword ptr ds:[0x549ED8]
0048C067 . |890424 mov dword ptr ss:[esp],eax
0048C06A . |E8 91DCFFFF call jiubugao.00489D00 ; bsae64解密口令
0048C06F . |8B4424 10 mov eax,dword ptr ss:[esp+0x10]
0048C073 . |8B4C24 0C mov ecx,dword ptr ss:[esp+0xC] ; ntdll_12.77C458C5
0048C077 . |8B5424 14 mov edx,dword ptr ss:[esp+0x14]
0048C07B . |8B5C24 18 mov ebx,dword ptr ss:[esp+0x18]
0048C07F . |85DB test ebx,ebx
0048C081 . |0F85 59010000 jnz jiubugao.0048C1E0
0048C087 . |890C24 mov dword ptr ss:[esp],ecx
0048C08A . |894424 04 mov dword ptr ss:[esp+0x4],eax
0048C08E . |895424 08 mov dword ptr ss:[esp+0x8],edx
0048C092 . |8B4424 2C mov eax,dword ptr ss:[esp+0x2C] ; kernel32.770200E8
0048C096 . |894424 0C mov dword ptr ss:[esp+0xC],eax
0048C09A . |C74424 10 100>mov dword ptr ss:[esp+0x10],0x10
0048C0A2 . |C74424 14 100>mov dword ptr ss:[esp+0x14],0x10
0048C0AA . |E8 D1FBFFFF call jiubugao.0048BC80 ; aes解密
0048C0AF . |8B4424 24 mov eax,dword ptr ss:[esp+0x24]
0048C0B3 . |8B4C24 1C mov ecx,dword ptr ss:[esp+0x1C] ; kernel32.77020000
0048C0B7 . |8B5424 18 mov edx,dword ptr ss:[esp+0x18]
0048C0BB . |85C0 test eax,eax
0048C0BD . |0F85 D9000000 jnz jiubugao.0048C19C
0048C0C3 . |83F9 1A cmp ecx,0x1A ; 解密后为26个字符
0048C0C6 . |74 7E je short jiubugao.0048C146 ; 跳走
4.通过分析发现sha的取值是输入的uid的,输入的口令先用base64解密,然后再aes解密。
5.在 【0048C0AA . E8 D1FBFFFF call jiubugao.0048BC80 ; aes解密 】处下断点,看一下解密函数的构造,有6个参数,堆栈里有关键的出现,具体如下图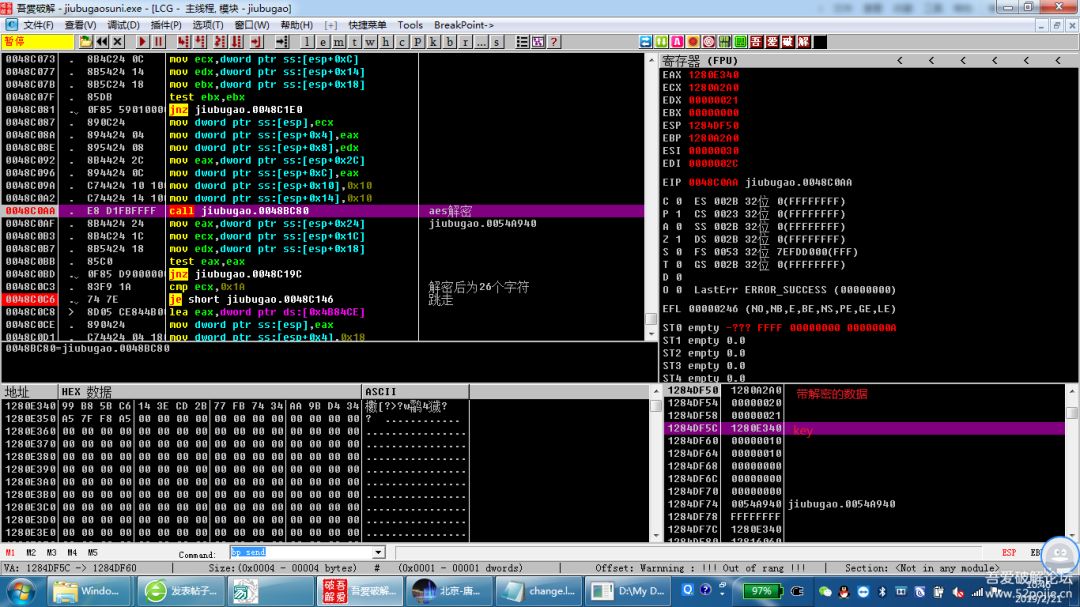
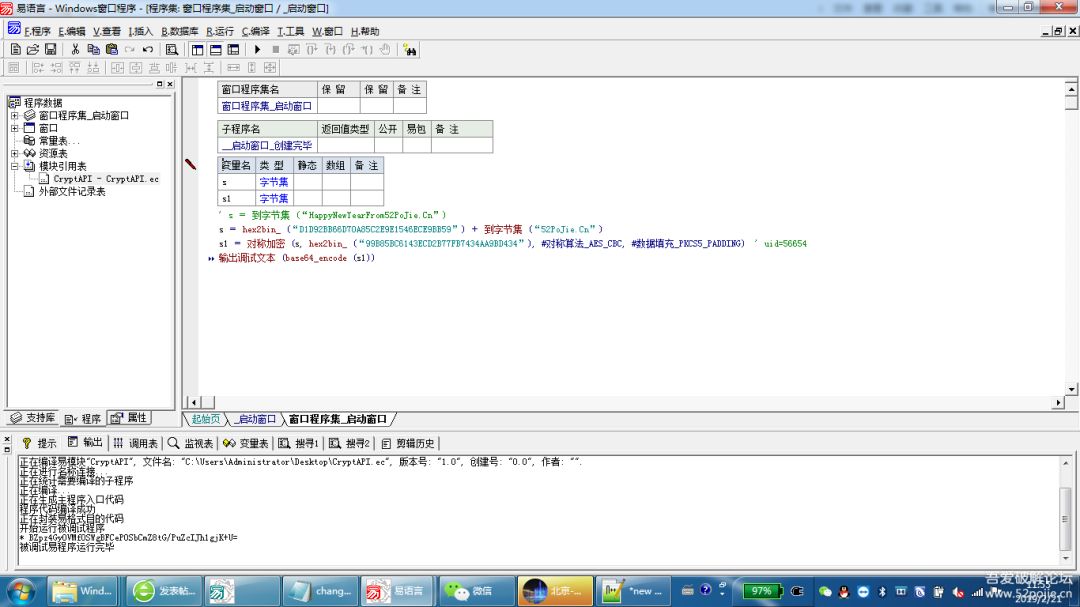
6.key就是aes解密的key了,但是根据参数来,应该是16为(0x10),有了基础数据,就可以尝试生成key了。编程功底不好,随便拿e语言写了个,将就看。
首先根据uid(56654),得到了key,然后用自己写的加密程序,将“HappyNewYearFrom52PoJie.Cn”经过aes加密【CBC、_PKCS5_PADDING】,再经过base64编码,得到【F39N9NEefmp/zJ8T9sN6AD8bEuhG7b56rR+G1+t/CKg=】,输入到口令出,发现不行(这个可能是e语言aes加密方式和golang不一样所导致)。。。失败了。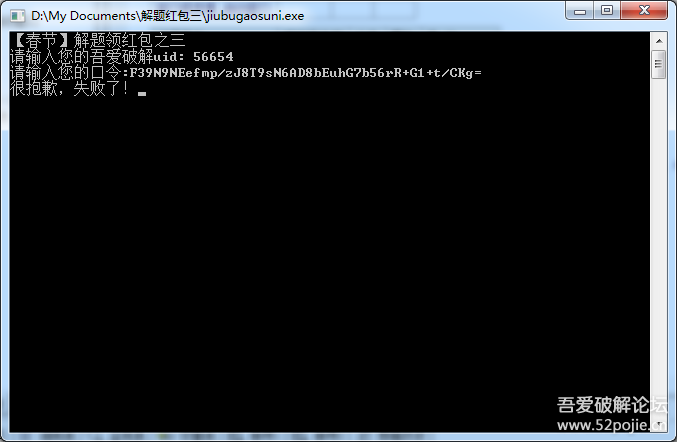
7.继续深入的找一下,发现了一个出现解密结果的地方,果断下段,分析一下,看看情况。
004892B7 . E8 24F2FFFF call jiubugao.004884E0 ; ?
004892BC . 83C4 24 add esp,0x24
004892BF . C3 retn ;下断点,看堆栈第三行数据
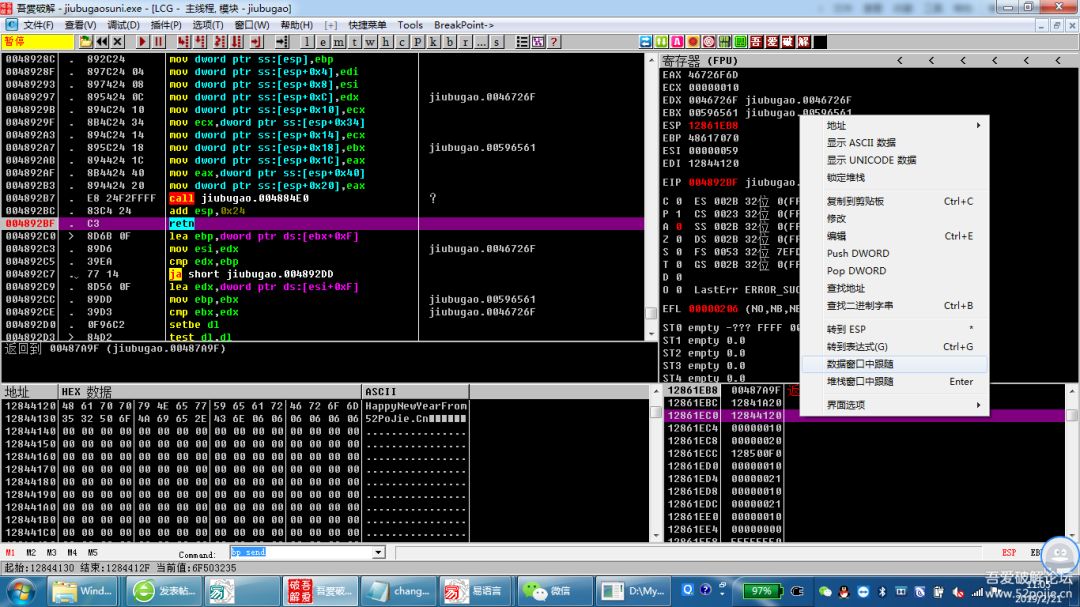
8.看到解密后的是我们所需要的,继续往下跟f8几下,发现第一行变了,进入变形算法call再跟,发现 关键变形算法是xor edi,ebp。
00487AC3 . 895424 04 mov dword ptr ss:[esp+0x4],edx
00487AC7 . 8B5C24 3C mov ebx,dword ptr ss:[esp+0x3C]
00487ACB . 895C24 08 mov dword ptr ss:[esp+0x8],ebx
00487ACF . 894C24 0C mov dword ptr ss:[esp+0xC],ecx
00487AD3 . 895424 10 mov dword ptr ss:[esp+0x10],edx
00487AD7 . 895C24 14 mov dword ptr ss:[esp+0x14],ebx
00487ADB . E8 80020000 call jiubugao.00487D60 ; 变形算法
00487AE0 . 8B4424 58 mov eax,dword ptr ss:[esp+0x58]
00487AE4 . 8B48 20 mov ecx,dword ptr ds:[eax+0x20]
00487AE7 . 8B50 1C mov edx,dword ptr ds:[eax+0x1C]
00487AEA . 8B58 18 mov ebx,dword ptr ds:[eax+0x18]
00487CC0 |. 8B6CB5 00 ||mov ebp,dword ptr ss:[ebp+esi*4] ; 关键变形算法
00487CC4 |. 31EF ||xor edi,ebp
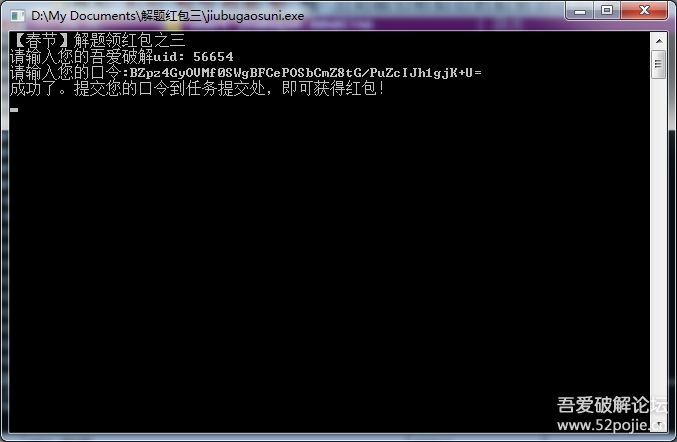
9.把变形后的二进制复制出来,将hex2bin_ (“D1D92BB66D70A85C2E9E1546ECE9BB59”) + 到字节集 (“52PoJie.Cn”),经过aes加密【CBC、_PKCS5_PADDING】,再经过base64编码,得到【BZpz4GyOVMf0SWgBFCePOSbCmZ8tG/PuZcIJh1gjK+U=】,再次输入uid和口令,成功。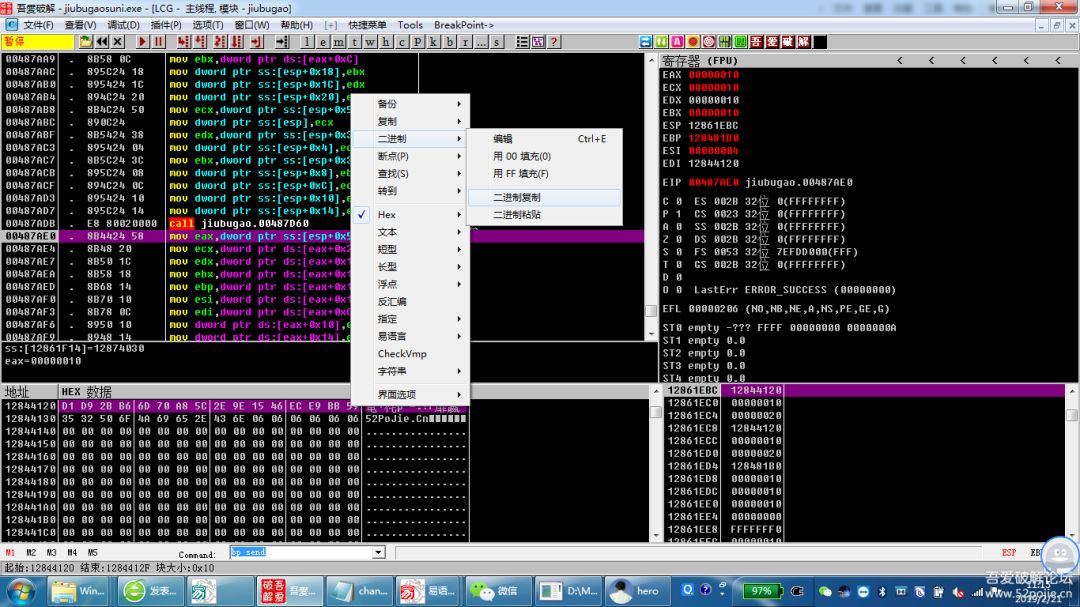
第二题OD分析可以直接去论坛查看,不推送啦~
【原创】春节红包第二题-writeup-od版
https://www.52pojie.cn/thread-874670-1-1.html
--官方论坛
www.52pojie.cn
--推荐给朋友
公众微信号:吾爱破解论坛
或搜微信号:pojie_52
文章评论